Modern tech stack is a dynamic blueprint that blends people, processes, and technology to deliver faster, more reliable software that can adapt to changing user needs and business goals. From cloud to edge computing, this landscape orchestrates compute and data across centralized clouds and nearer-to-user edge nodes, enabling applications that scale with demand while maintaining consistent behavior. Organizations lean on cloud-native development practices to build scalable services that can run across environments, with automated testing, gradual rollouts, and clear rollback paths. Edge AI and analytics empower real-time insights and personalization by moving inference closer to where data is produced, reducing latency and supporting scenarios with intermittent connectivity. Across the stack, security is embedded through identity, encryption, access controls, and governance, ensuring trust and resilience as workloads shift between cloud and edge.
In other terms, this approach is a cloud-edge continuum—a cohesive software ecosystem that merges centralized processing with localized computing near devices. Think of it as a hybrid software fabric where microservices, containers, and orchestration work together to deliver consistent behavior across on-premises data centers and edge gateways. The objective remains consistent: low latency, scalable deployment, and robust security, achieved through interoperable APIs, standardized data contracts, and governance that travels with the data. Viewed through the lens of modern architecture, this strategy translates into edge‑aware patterns such as tiered processing, local data retention, and federated identity across environments.
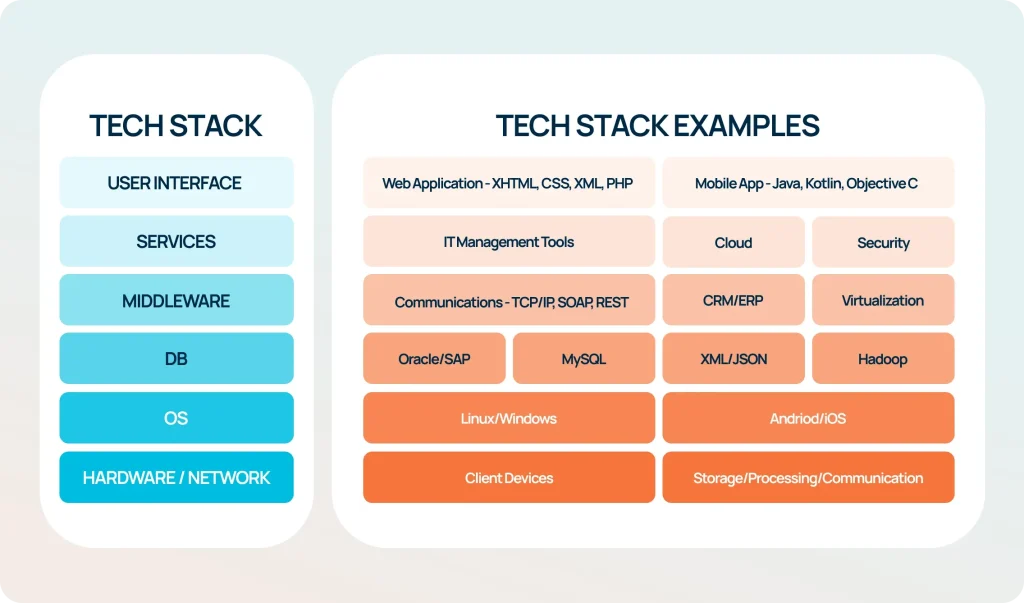
Modern tech stack for cloud to edge computing: architecture, security, and cloud-native development
A modern tech stack blends cloud services with edge resources to enable a cohesive flow of data and compute across locations. In cloud to edge computing, edge computing architecture places processing closer to where data is generated, delivering real-time insights while the cloud handles heavier workloads such as large-scale analytics, governance, and long-term storage. Cloud-native development practices—stateless services, containerization, and orchestrators like Kubernetes—facilitate consistent deployment, portability, and resilience across both environments.
Security and governance are embedded in every layer of the stack. By applying zero trust, encryption in transit and at rest, and robust identity management, organizations can maintain strong security as workloads shift between cloud and edge. Observability, CI/CD pipelines, and formal governance ensure that data flows, policy enforcement, and auditing stay coherent across the distributed system, preserving reliability even as processing moves closer to users.
Edge AI and analytics in distributed systems security: how to design resilient cloud to edge workflows
Edge AI and analytics enable real-time inference and decision-making at or near the data source, reducing latency and bandwidth usage. In a cloud to edge strategy, the edge handles time-sensitive processing while the cloud supports model training, versioning, and centralized analytics. This combination relies on a deliberate edge computing architecture that coordinates workloads across devices, gateways, and regional nodes, ensuring that insights are timely and contextually relevant.
Distributed systems security becomes paramount as compute, data, and control span cloud and edge. Implementing a zero-trust posture, managing short-lived credentials, and enforcing robust key management help protect data in transit and at rest across environments. Governance of data lineage, access controls, and policy enforcement must extend from cloud down to edge nodes, with comprehensive observability and auditing to maintain resilience in the face of intermittent connectivity and varying edge capabilities.
Frequently Asked Questions
How does a modern tech stack enable cloud to edge computing and real-time processing?
A modern tech stack unifies cloud services and edge resources into a coordinated platform. The cloud handles scalable storage, analytics, and central governance, while the edge executes time-sensitive tasks and real-time inference—enabled by edge computing architecture. Containerization with Docker and orchestrators like Kubernetes provide consistent deployment across environments, while cloud-native development and CI/CD pipelines accelerate safe delivery. Observability and security are embedded at every layer, with strong identity, encryption in transit and at rest, and a zero-trust approach guiding access between services and nodes. This combination reduces latency, conserves bandwidth, and supports real-time decision-making from cloud to edge.
What security and governance considerations are essential in a modern tech stack spanning cloud and edge?
Security and governance should be baked into every layer of a modern tech stack that spans cloud and edge. Embrace distributed systems security and a zero-trust model with unified identity and access management, short-lived credentials, and robust key management across environments. Encrypt data in transit and at rest, and apply consistent policy enforcement with edge computing architecture and cloud-native development practices. Enforce data governance across both layers—data lineage, retention, privacy, and regulatory compliance—while maintaining observability and incident response to quickly detect and mitigate threats, including for edge AI and analytics workloads.
| Aspect | Key Points |
|---|---|
| Definition / Goals | A cohesive architecture that enables speed, reliability, and adaptability; supports a cloud-to-edge spectrum; enables real-time processing, reduced bandwidth, and personalized experiences with governance. |
| Core components | Cloud services, edge resources, and a well-engineered software pipeline. Includes containerization (Docker), Kubernetes, CI/CD, observability, and security with zero-trust principles. |
| Cloud to Edge patterns | Tiered architecture linking edge nodes with central cloud; edge AI inference; compute near users; reduced data gravity; enhanced resilience and latency. |
| Cloud Layer | Scalable storage, data lakes/warehouses, serverless, identity and security services, networking; stateless, scalable services; platform for CI/CD, monitoring, and governance. |
| Edge Layer | Compute near data generation; real-time analytics; local data retention; edge AI; privacy considerations; security via local policies and reduced exposure. |
| Networking & Security | Secure data flow between cloud and edge; federated identities, short-lived credentials, robust key management; encryption in transit and at rest; zero-trust; cross-layer observability. |
| Data Management & Governance | Data sovereignty, privacy, and compliance; lifecycle policies and lineage tracking; consistent policies for data retention, access controls, and auditability from cloud to edge. |
| Best Practices | Start with workloads; adopt a phased rollout; standardize data formats and interfaces; invest in automation and testing; prioritize security and resilience across the stack. |
| Case Study Idea | Retailer example: real-time personalization via edge processing at point of sale, cloud analytics for group insights, and governance for model updates and privacy. |
| Future Trends | More services at the edge; distributed orchestration; modular, event-driven architectures; serverless at the edge; smaller AI models and smarter edge gateways. |
Summary
Modern tech stack concepts spanning cloud to edge provide a blueprint for building responsive, secure, and scalable software systems. By aligning cloud capabilities with edge resources, organizations can reduce latency, improve resilience, and unlock real-time analytics. A holistic design that emphasizes governance, security, and interoperable components helps developers and operators deliver personalized experiences at scale.